Achieving CMMC 2.0 Compliance With A Shared Responsibility Model: Q & A
This blog contains curated questions and answers pertaining to achieving CMMC 2.0 compliance with A Shared Responsibility matrix.
Department of Defense contractors and those in higher education research facilities are moving to external services providers to satisfy current federal mandates such as CMMC 2.0, NIST 800-171, and DFARS 7012. These suppliers are faced with critical decisions when it comes to outsourcing compliance because of industrial complexities and the potential lack of operational resources.
The most current mandate, CMMC 2.0, requires contractors and those handling sensitive data (CUI/CDI/CTI/ITAR) on behalf of the DoD to define obligations and responsibilities when using external service providers.
Many of the questions and answers in this blog are derived from a recent Summit 7 webinar: Achieving CMMC 2.0 Compliance With The Shared Responsibility Model. The inquiries came from a group of over 600 suppliers in the Defense Industrial Base (DIB). Portions of the webinar were recorded and released on the Summit 7 YouTube channel and are also linked and embedded throughout this article. You can view the entire webinar here. Make sure you subscribe to the Summit 7 YouTube channel to stay informed on all things related to the DIB and CMMC 2.0.
You can download a version of the Summit 7 Shared Responsibility Matrix here.
/Summit-7-SRM-Thumbnail.png?width=1921&name=Summit-7-SRM-Thumbnail.png)
Click on any of the topics below to jump to a topical section in this blog. You will find questions related to that topic followed by the answer given by the Summit 7 leadership team:
-
The Shared Responsibility Model (SRM) and CMMC Assessments
-
CMMC 2.0 and Controlled Unclassified Information (CUI)
-
Reporting SPRS Scores For CMMC
-
FedRAMP Solutions and NIST 800-171
-
M365, AWS, and GCC High For CUI
The Shared Responsibility Model (SRM) and CMMC Assessments
-
What is the Shared Responsibility Model?
-
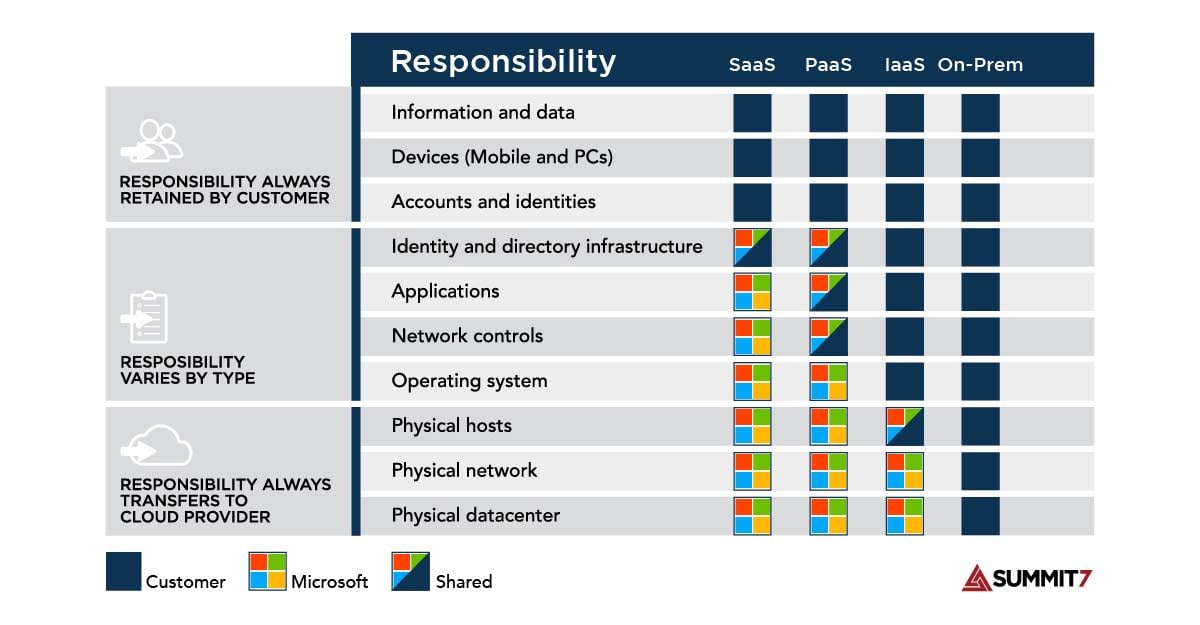
The Shared Responsibility Model (SRM) is the natural capturing, identifying, and dividing of responsibilities between customers and providers.
-
It specifically identifies the person or team responsible for any given security control; most importantly, the responsibility needs to be agreed upon and reflected in contracts or service level agreements.
-
-
Is a Shared Responsibility Model required for DIB contractors?
- If an organization is currently using external service providers, then they need to be asking those service providers for a shared responsibility model according to NIST SP 800-171.
- 74% of the Defense Industrial Base (DIB) is comprised of small businesses, most of which rely on cloud-based, outsourced third-party solution providers. Many of these organizations are under the impression that they are under an agreement where they have no responsibilities specific to compliance; these organizations will quickly be surprised when their service level agreement terms do not match up with the expectations of their external service providers.
The video below gives a brief explainer on data governance and the Summit 7 Shared Responsibility Model.
- If an organization is currently using external service providers, then they need to be asking those service providers for a shared responsibility model according to NIST SP 800-171.
-
Who needs to be using a Shared Responsibility Model (or Matrix)?
-
If you are a company that needs to implement NIST 800-171 controls in order to comply with federal regulations, and you use any outsourced services (i.e. cloud, I.T., security), then you already are using a concept of the Shared Responsibility Model - a fundamental concept of cloud security.
It is the idea that the level of service you are consuming from an external provider influences the amount of control that either you or the provider have over those services.
Your level of responsibility is impacted depending on how many services you are acquiring from an external provider.
A Shared Responsibilities Matrix will be utilized by Summit 7 and our customers based on the customer's particular level of engagement with our team. You can learn more about Summit 7's SRM by contacting our Managed Services team here.
-
-
Does this SRM also extend to application development entities?
-
Yes, this model would extend to anyone or any platform within the security boundary for handling Controlled Unclassified Information (CUI).
-
-
Do you have a summary of which practices in the RACI have dependencies on Microsoft Azure vs. Summit 7 as a provider?
-
The Summit 7 Shared Responsibility Matrix details this specific question. You can download the Summit 7 Shared Responsibility Matrix here.
-
-
Are Shared Responsibility Matrices something that can be obtained from various service providers?
-
Some providers have SRMs out there, or they are currently working on one. If you are working with a Managed Service Provider (MSP), you should be asking to see their SRM according to NIST 800-171.
-
-
Are there examples of a Shared Responsibility Matrix?
-
If you are running an entirely on-premises IT system, then you do everything. You're responsible for physical security and all the way up to software and applications.
-
If you were just consuming software applications as a service (SaaS), everything except for what is inside of that application is the responsibility of the provider.
Video: Are there examples of a CMMC SRM?
-
-
Would the best way to capture compliance with all Assessment Objectives (AOs) be mapping all AOs to written procedures capturing the Administrative/Physical/Logical control implementation and mapping those written procedures back to written policy outlining roles and responsibilities within the SRM?
-
There is no requirement to have written procedures for every determination statement in NIST SP 800-171. However, if you have the time and resources, then a useful technique is to treat each of the 320 determination statements as a question.
-
For example, converting 3.1.1[a] into a question would ask: "How are authorized users identified?" The documented answers to determination statements would roughly represent your procedures for a given control. Logically, the roles and responsibilities assigned to these tasks should be found via your approach to policies in general.
-
-
How does RACI distinguish "responsible" from "accountable"?
-
The responsible person is the one actually doing the task. The accountable person is the one that is ultimately accountable for ensuring that the task is completed.
-
-
Can evidence for the SRM be verbal or does it need to be documented? My manager feels verbal is enough, but my stance is that verbal cannot be audited and made repeatable.
-
It's based specifically on each control. There are three different determinants for verbal, so it varies by control.
-
There are some controls that can verbally be satisfied, but you need to see which ones those are and what the other statements are in that control.
-
CMMC 2.0 and Controlled Unclassified Information (CUI)
-
Why spend money on CMMC 2.0 before final rules are established?
-
Requirements have been in place with DFARS 7012 since 2017, and you have contractual requirements to meet these requirements today.
-
CMMC is adding the third-party assessment piece to these requirements. You already have the requirements and the data, and you should already be fulfilling these requirements.
-
There won't be enough C3PAOs and other similar resources once the final ruling is done to get everyone assessed and ready to do business with the government.
-
-
What is the value of CMMC given the shifts created by CMMC 2.0? This essentially said we are returning to the NIST 800-171 assessments.
-
CMMC is an assessment methodology for NIST 800-171.
-
DFARS 7012 requires the basic self-assessment.
-
DFARS 7019/7020 ushered in government assessments of NIST 800-171 and DFARS 7021/CMMC will implement third party assessment requirements for NIST 800-171.
-
-
What role does application vulnerability scanning play in CMMC 2.0?
-
RA.L2-3.11.2 states: "Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified."
-
There are 5 assessment objectives for this control.
-
-
How long does it take for a company to achieve CMMC 2.0 Level 1/2/3?
-
The process is very dependent on the current state and size/complexity of the organization.
-
For a small-medium business, it typically takes 9-15 months to complete everything necessary.
- Read more on CMMC 2.0 and timelines for implementation here.
-
-
Do you have an idea of the cost of CMMC 2.0 compliance for a very small business (1-30 employees)?
-
This is highly variable depending on the current state of the small business.
-
If you take into consideration internal labor, consultant labor, hardware/software, etc., it is a minimum $100K+ task to go from zero to complete/operational.
-
-
Do you have any thoughts on whether the rulemaking process may be further delayed to incorporate or align with the FAR CUI rule and the Biden EO which is pushing ZTA and FedRAMP updates?
- The rulemaking process for both CMMC rules shouldn't be delayed by the FAR CUI rule.
- The FAR CUI rule will codify NIST SP 800-171 as the minimum baseline for the protection of CUI for all federal contractors via a contract clause.
- The FAR CUI rule will also specify how CUI is to be identified in contracts - a critical missing piece over the last few years. The FAR CUI rule is expected early in 2022, several months ahead of when we anticipate the publication of the CMMC rules.
- Any changes to NIST SP 800-171 for ZTA wouldn't affect the rules which "wrap" around NIST guidance, so to speak.
Reporting SPRS Scores For CMMC
-
Are we supposed to report on CMMC in SPRS on the 110 controls or the 320 Assessment Objectives?
-
You must evaluate all 320 Assessment Objectives. If a 5 point control has 5 Assessment Objectives, you must successfully implement all 5 assessment objectives to award yourself the 5 points for the control.
-
For an in-depth look at this, you will want to watch this video from thought-leader Jacob Horne at a recent Cloud Security and Compliance Series (CS2) session.
The video below gives a short explanation on submitted SPRS scores against the 320 AOs.
-
-
What are typical/average SPRS scores based on the 110 controls in NIST 800-171 vs. based on the 320 Assessment Objectives?
-
DoD has not released any statistics around SPRS scores.
-
-
How do you figure out your score using SPRS score methodology to capture each determination statement?
-
You must follow NIST 800-171A and the DoD assessment methodology.
-
FedRAMP / NIST 800-171
-
A real challenge in meeting DFARS 7012 and CMMC is understanding what cloud environments and services will be acceptable given the "equivalent standards" wording. FedRAMP authorized environments/products are simply "unattainable" for some companies. Do you have any insight given this is foundational underlying the shared responsibility model?
-
Since 2016 DFARS clause 252.204-7012 has said that if a contractor puts CUI in the cloud then the contractor needs to require and ensure that the cloud service provider meets security requirements "equivalent" to the FedRAMP Moderate baseline.
On 12/21/23, the DoD released a memo clarifying the stringent requirements of FedRAMP moderate “equivalency”– and it’s effective immediately. DoD Contractors are now on the hook for their Cloud Service Provider’s (CSP) FedRAMP compliance. According to the memo: the DoD requires a lot of contractors with defense data being stored, processed, or transmitted with a FedRAMP Equivalent CSP.
A FedRAMP Moderate Authorized CSP will require considerably less effort by the contractor. You can check if your CSP is Authorized on the FedRAMP marketplace. If you do have an FedRAMP moderate "equivalent” CSP, you might consider switching to a FedRAMP-Tailored Solution. We recommend either Microsoft GCC or GCC High.
-
-
Could you elaborate on companies abroad (outside the US) in relation to FedRAMP?
-
FedRAMPed services are available to companies and organizations from around the world. An organization does not have to be in the United States to leverage FedRAMPed services.
-
-
Has there been any indication as to when NIST SP 800-171 Rev 3 will be expected?
-
NIST has not announced a specific release window for NIST SP 800-171 Rev 3 other than sometime in 2022.
-
-
Isn't it onerous that the DIB has to meet ALL 800-171 controls while the Federal Government can use risk waivers for their required controls?
-
NIST 800-171 is the control baseline for protecting CUI in non-federal information systems.
-
There is no bar below 800-171 that would meet the requirement. NIST 800-53 (the government standard for federal information systems) has many more controls and requirements than NIST 800-171 and does provide for some tailoring of controls.
-
-
If you only want to achieve CMMC 2.0 Level 1 compliance, do you still have to meet all of the NIST 800-171A requirements?
-
No, you would only need to meet the 17 Level 1 controls and the associated Assessment Objectives.
-
-
What are the controls that a 3rd party provider can't do?
-
There are many, but most revolve around defining corporate policy.
-
-
Where can I find information on NIST 800-171A?
M365, AWS, and GCC High For CUI
-
Do you ever work with AWS resources to meet compliance requirements? Especially for cloud-only workloads? If so, how do you find it compared to M365?
-
Summit 7 focuses primarily on the Microsoft stack only, and one reason is because of the SaaS solution. AWS really compares well to Microsoft Azure, but Amazon does not really have a comparable platform to the M365 platform (SaaS-based email, file-sharing, etc.).
-
Microsoft's total solution of M365 plus Azure Government gives you a really nice, single platform solution to be able to meet all of these requirements.
Video: Does Summit 7 work with AWS for cloud-based compliance?
-
-
What is your opinion on international MSPs (Canada) within the Shared Responsibility Matrix and the administration of an on-prem IS containing CUI? Additionally, with control MP.L2-3.8.9 – PROTECT BACKUPS, can data be backed up on company-owned servers residing in Canada?
-
There is no problem with backing up to company-owned servers in a company-owned facility with all of the necessary NIST 800-171 controls in place.
-
There is no problem with a Canadian MSP servicing the customer as long as the MSP is meeting all of the necessary CMMC requirements and the customer is not handling any export-controlled/ITAR or NOFORN data.
-
If they are handling the aforementioned data, then the MSP employees would need to either be US citizens or they would need to have specific export control licenses for the data allowing them access.
-
-
Is M365 considered a MSP?
-
Microsoft is a Cloud Solution Provider and their environments are FedRAMPed. They are not a Managed Service Provider.
-
-
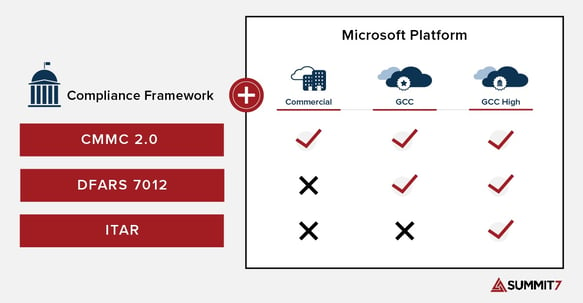
Do you still recommend GCC High for all CUI?
-
Yes, we do recommend GCC High and Azure Government for all CUI. It is a requirement for all ITAR/Export Controlled content, but a recommendation for Basic CUI.
-
-
Regarding the 89% managed in Summit 7's Shared Responsibilities Model, do you assume the company is only on GCC High with you? What resources are assumed to be on-premises?
-
It does not take into consideration any on-premises infrastructure or any other cloud services you may have outside of the Microsoft Azure Government stack.
-
-
Does Summit 7 have a surcharge for MSP services delivered to NIST/CMMC clients?
-
We only service NIST/CMMC clients, so there is no upcharge for Summit 7 MSP services.
-
Video: Managed Services for CMMC 2.0 Compliance
You can contact our team about Managed Services through Summit 7 via the button below.