CIRCIA Rulemaking and Double Incident Reporting for the DIB
CISA issued a 457-page proposed rule implementing the 2022 Cyber Incident Reporting for Critical Infrastructure Act. Unless CISA and DoD can reach an agreement, DIB contractors will have duplicative incident reporting obligations for two different agencies.
Watch the Podcast
What is CIRCIA?
In response to the ransomware attack on Colonial Pipeline, Congress passed the Cyber Incident Reporting for Critical Infrastructure Act. “CIRCIA” directs CISA to conduct rulemaking and issue a regulation establishing comprehensive cyber incident reporting requirements across the various critical infrastructure sectors.
What is the impact of CIRCIA on the DIB?
The Defense Industrial Base is designated as a critical infrastructure sector and defense contractors have had cyber incident reporting obligations pursuant to DFARS clause 252.204-7012 for many years. But CISA’s 457-page proposed rule both duplicates and expands existing DFARS reporting requirements.
Unless CISA and DoD can reach an agreement, DIB contractors will have duplicative incident reporting obligations for two different agencies.

What is a summary of CIRCIA?
Public comments are due by June 3rd, 2024.
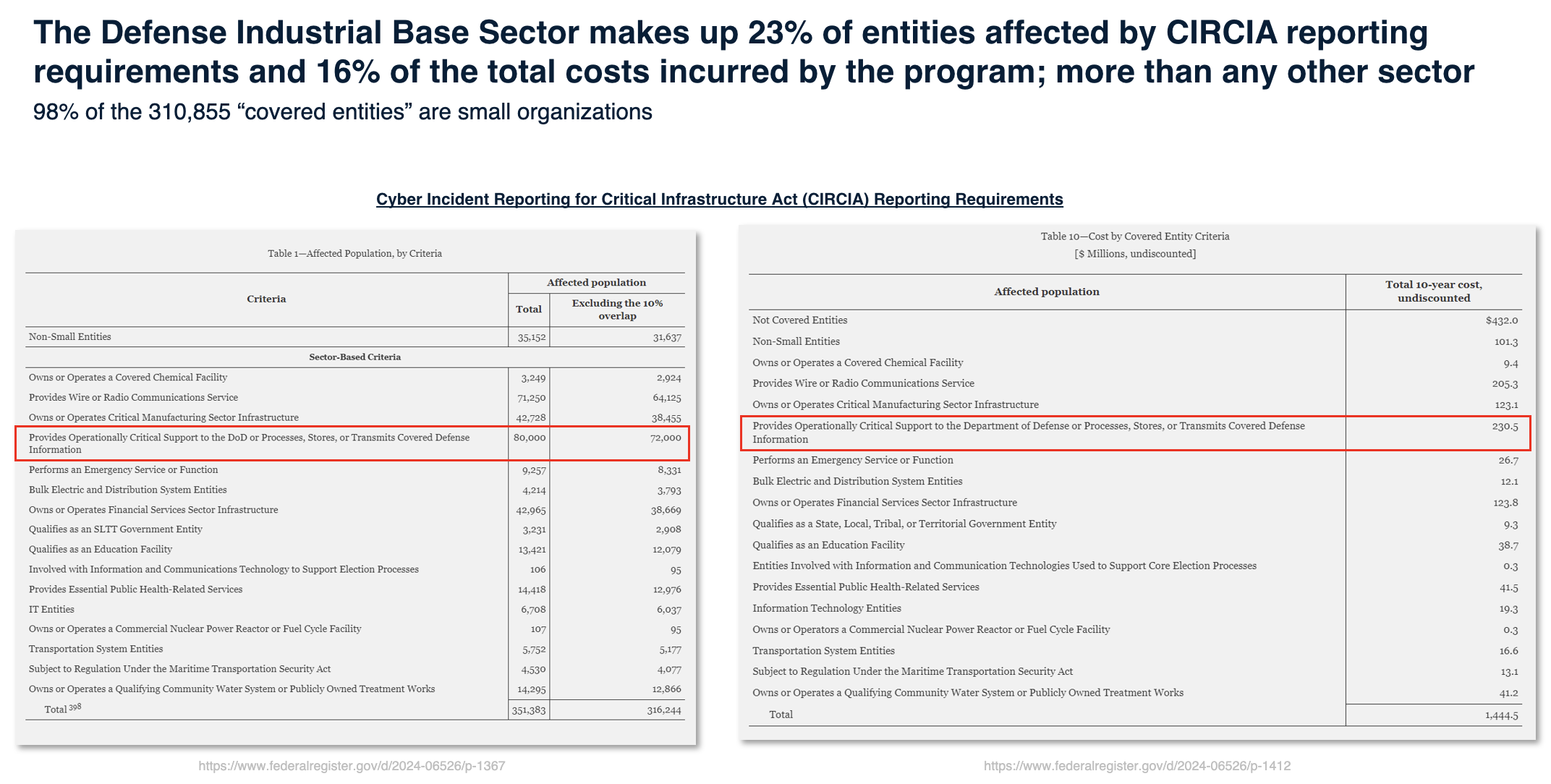
CISA estimates the rule will affect 316,244 entities across 13 of the 16 critical infrastructure sectors.
The DIB makes up 23% of all affected entities and 16% of total program costs (a cool $1.4B).
98% of affected entities are small organizations.
The CIRCIA legislation requires the final rule to be issued 18 months after the proposed rule so expanded requirements aren’t closer than people think.
If you don’t have time to read the full rule, check out the official summary from the Congressional Research Service.
The proposed rule outlines 4 types of mandatory reports
- Covered Cyber Incident Report
- Ransomware Payment Report
- Joint Covered Cyber Incident or Ransom Payment
- Supplemental Report
CIRCIA Covered Cyber Incidents are much broader than under DFARS 252.204-7012
- Must be reported within 72 hours
- Defined as “a substantial cyber incident experienced by a covered entity”
- “Substantial Incident” is defined as incidents with any of the following 4 types of “impacts”:
- Substantial Loss of Confidentiality, Integrity, or Availability
- Serious Impact on Safety and Resiliency of Operational Systems and Processes
- Disruption of Ability to Engage in Business or Industrial Operations
- Unauthorized Access Facilitated Through or Caused by a compromise of a CSP, MSP, or Other Third-Party Data Hosting Provider, or Supply Chain Compromise
- DFARS 252.204-7012(c) is only concerned with incidents related to compromised Controlled Unclassified Information or the systems that store, process, or transmit CUI (“covered contractor information systems”).
- This disparity in scope means that defense contractors will see expanded incident reporting obligations even if CISA and DoD agree only a single reporting interface.
There are penalties for not reporting incidents under CIRCIA
If an organization fails to respond to an incident report RFI, CISA can subpoena you. False Claims made during this process can be referred to the Department of Justice.
Managed Service Providers (MSPs) get a full legal definition
“An entity that delivers services, such as network, application, infrastructure, or security services, via ongoing and regular support and active administration on the premises of a customer, in the data center of the entity (such as hosting), or in a third-party data center.”
MSPs can be authorized to report incidents on behalf of the clients however it seems likely that this will be a point of legal and contractual contention without careful negotiation.
Section 226.7 - Required Information for CIRCIA Reports
“If a covered entity uses a third party to submit a CIRCIA Report on the covered entity's behalf, an attestation that the third party is expressly authorized by the covered entity to submit the CIRCIA Report on the covered entity's behalf."
Episode Links:
- CIRCIA Proposed Rule: https://www.federalregister.gov/docum...
- Congressional Research Service Report (PDF): https://crsreports.congress.gov/produ...
- 7 Tips for Crafting Good Public Comments
Sum IT Up Podcast
With Jacob Horne and Jason Sproesser
We sum up the news and developments relevant to CMMC, DFARS, and NIST standards such as SP 800-171, SP 800-53, the NIST Cybersecurity Framework, and others.