7 Things to Know About the Latest NIST Security Requirements (Final Public Draft of NIST SP 800-171 Revision 3)
NIST has released the final public draft (FPD) of SP 800-171 revision 3 and the initial public draft (IPD) of SP 800-171A revision 3.
NIST has released the final public draft (FPD) of SP 800-171 revision 3 and the initial public draft (IPD) of SP 800-171A revision 3. These will be the last drafts (and the last public comment window) before the revisions become final in Spring 2024. The road to CMMC certification runs through NIST SP 800-171 and SP 800-171A. What do the latest drafts reveal about the path forward for defense contractors?
TL;DR
The final draft of NIST SP 800-171 revision 3 only contains 95 requirements. However, the overall level of effort compared to the existing 110 requirements in has increased. Here's a quote from the SUMMITUP Podcast to simplify: "You must orient your program around NIST SP 800-171 A (the assessment objectives) if you want to be successful in your CMMC assessment."
Here are 7 things you need to know about the coming changes to cybersecurity requirements for Controlled Unclassified Information (CUI):
1) Formatting changes obscure the overall increase in the final draft of NIST SP 800-171r3.
There are 95 requirements in NIST SP 800-171r3 (FPD). This is a 14% decrease compared to the 110 requirements in NIST SP 800-171r2.
There are 44 organizationally defined parameters (“ODPs”) in the 171r3 final draft. This is a 60% decrease compared to the 100+ ODPs in the initial draft of SP 800-171r3.
While these decreases are described by NIST as “significant”, they are an illusion just like they are currently in revision 2. 171r2 contained 110 requirements that were each only one line long. That is, 171r2 requirements appeared to only have a single “control item”. In contrast, 171r3 requirements often contain multiple control items.
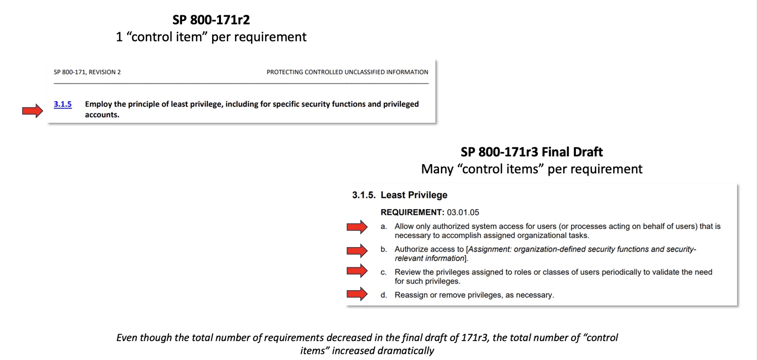
There are 266 individual controls items in the final draft of 171r3. This is a 142% increase compared to 171r2.
Obviously, something strange is going on here. The total number of requirements decreased while the total number of items in those requirements increased dramatically. In order to get a clear picture of what actually needs to be done and how large the revision 3 delta is, we have to dive into the initial draft of SP 800-171A revision 3.
If there is one thing you take from this blog, let it be this: you cannot gain a full understanding of NIST cybersecurity requirements by reading SP 800-171 alone.
2) SP 800-171A revision 3 increases significantly.
There are 445 total “determination statements” in 171r3 IPD. This is a 39% increase compared to the 320 determination statements currently in SP 800-171A.
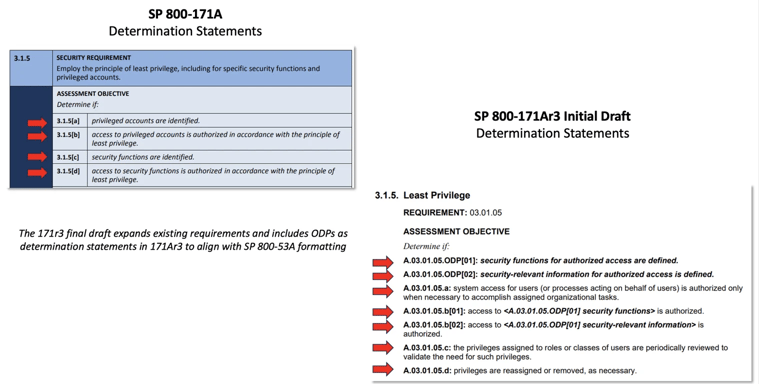
56 of the 445 verification steps are organizationally defined parameters (ODPs).
ODP verification is a fundamental aspect of SP 800-53A. The change in the draft of 171Ar3 reflects NIST’s overall move to directly align SP 800-171 and 171A with SP 800-53 and 53A, respectively.
Notice the disparity between 56 ODPs in 171Ar3 and 44 ODPs in 171r3. Organizations need to use both documents together or else they run the risk of significant surprises during their assessments.
Some examples of controls with ODP disparities include:
- 3.1.5 – Least Privilege
- 3.1.20 – Use of External Systems
- 3.2.1 – Awareness & Training (Literacy)
- 3.2.2 – Awareness & Training (Role-Based)
- 3.4.6 – Least Functionality
- 3.5.5 – Identifier Management
- 3.14.1 – Flaw Remediation
If you only count the 389 non-ODP verification steps that resemble a “normal” determination statement in 171r2, it’s still a 22% increase over the current standard.
3) When are contractors required to implement NIST SP 800-171r3?
First, remember that the documents released today are drafts, not the final revisions. NIST plans to publish the final revisions in Spring 2024. For defense contractors handling Controlled Unclassified Information, DFARS contract clause 252.204-7012 requires that contractor information systems, “shall be subject to the security requirements in [NIST SP 800-171] in effect at the time the solicitation is issued or as authorized by the Contracting Officer.”
This is a problem because unless DoD issues a temporary waiver for this piece of DFARS 7012 (known as a “class deviation”) defense contractors will be immediately subject to the 171r3 delta (and immediately out of compliance).
Check out the Sum IT Up podcast episode below where former Navy contracting officer Lauren Ayers goes into detail on class deviations.
Currently there is no indication from DoD that there will be a class deviation.
Contractors should plan for the worst (a significant increase in the number of items on your Plan of Action & Milestones (“POAM”) and hope for the best (a class deviation of at least 6 months).
4) What does this mean for CMMC rulemaking and when will contractors be assessed against NIST SP 800-171r3?
Long story short: the CMMC rule is not affected by revisions to the NIST CUI series of standards because they are frustratingly independent of one another.
While NIST plans to finalize SP 800-171r3 and 171Ar3 in Spring 2024, current CMMC rulemaking indicates that assessments will begin sometime in the first half of 2025.
DFARS 7012 requirements and CMMC are closely related, but they are different. CMMC assessments follow DFARS 7012 requirements in order to verify compliance. As a result, if DoD were to issue a class deviation for the 171r3 delta, then CMMC assessments would not include those requirements until at least the end of waiver period.
If there is no class deviation in the way, then CMMC could theoretically assess SP 800-171r3 assuming the training and assessment materials have caught up. There is a lot of time between Spring 2024 and Spring 2025 for that to happen.
Ultimately, the longer a contractor waits to get a CMMC assessment, the higher the likelihood that SP 800-171r3 will have permeated the CMMC/DFARS ecosystem and become the new (assessable) standard.
5) Organizationally defined parameters are here to stay.
Organizationally defined parameters have drawn more frustration with the drafts of 171r3 than any other change.
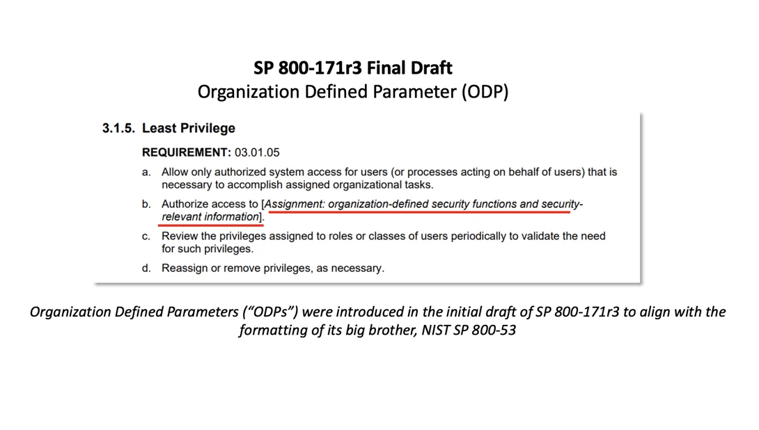
The 171r3 final draft includes an expanded explanation of ODPs - it’s worth reading closely:
- “Organization-defined parameters (ODPs) are included for some requirements. These ODPs provide flexibility through the use of assignment and selection operations to allow federal agencies and nonfederal organizations to specify values for the designated parameters in the requirements.”
- “Assignment and selection operations provide the capability to customize the security requirements based on specific protection needs. The determination of organization defined parameter values can be guided and informed by laws, Executive Orders, directives, regulations, policies, standards, guidance, or mission and business needs. Once specified, the values for the organization-defined parameters become part of the requirement.”
- “NIST does not establish or assign values for ODPs. If ODP values for selected security requirements are not formally established or assigned by a federal agency or a consortium of federal agencies, nonfederal organizations assign those values to complete the requirements.”
- “The term "organization" is used in many security requirements. The meaning of the term is context dependent. For example, in a security requirement with an ODP, an organization can refer to either the federal agency or the nonfederal organization establishing the parameter values for the requirement.”
The vast majority of ODPs are up to the contractor. However, DoD contractors need to be aware when external requirements stemming from regulations or contracts override their internal parameters.
For example, DFARS clause 252.204-7012(e) says, “When a Contractor discovers a cyber incident has occurred, the Contractor shall preserve and protect images of all known affected information systems … and all relevant monitoring/packet capture data for at least 90 days from the submission of the cyber incident report to allow DoD to request the media or decline interest.”
In this situation, if a cybersecurity requirement asked for an organizationally-defined time period for incident-related data retention, the contractor wouldn’t be able to choose a value shorter than 90 days. (Note: this external requirement exists whether 171 formatting contains ODPs or not.)
It’s possible that DoD will issue guidance on specific and/or recommendation ODP values. Contractors should keep their ears open as the final revision of SP 800-171r3 gets closer in Spring 2024.
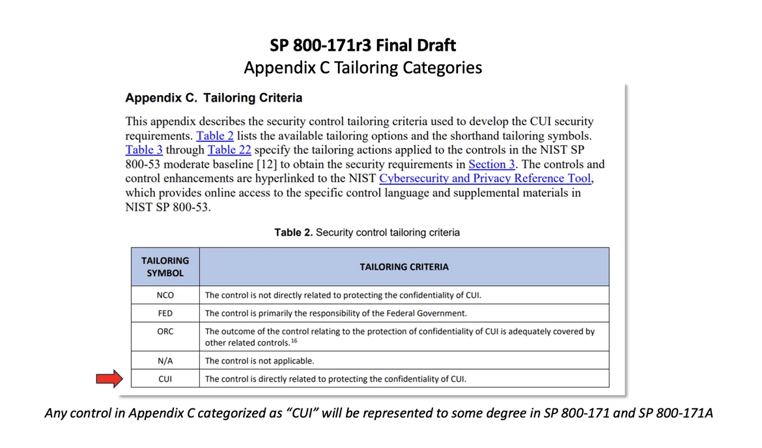
6) Public comments matter and they absolutely affect the substance and structure of SP 800-171 and 171A.
NIST has demonstrated their receptiveness to public comments in two ways:
First, the most common theme in the 2022 pre-draft call for comments was the recommendation that NIST eliminate the “NFO” control category. “NFO controls” are those 800-53 security controls that are “expected to be implemented by nonfederal organizations without specification”. Over the years, NFO controls have proven to hurt more than they help because unless a requirement is specified as such, organizations will often skip them.
Second, the most common theme in the public comments on the 171r3 initial public draft was the recommendation to reduce or eliminate the use of Organizationally Defined Parameters. Much of the final draft of SP 800-171r3 can be characterized by NIST’s efforts to implement these recommendations.
This time around, NIST is interested in comments on the following:- Re-categorized controls (e.g., controls formerly categorized as NFO).
- The new tailoring category for security controls that are addressed by other related security controls (“ORC”)
- The elimination of selected ODPs where the ODP specification did not significantly impact the security requirement.
- The combination of security requirements (or parts of requirements) for consistency and ease of use.
- Re-sequencing the content of discussion sections to align with the individual parts of the requirements.
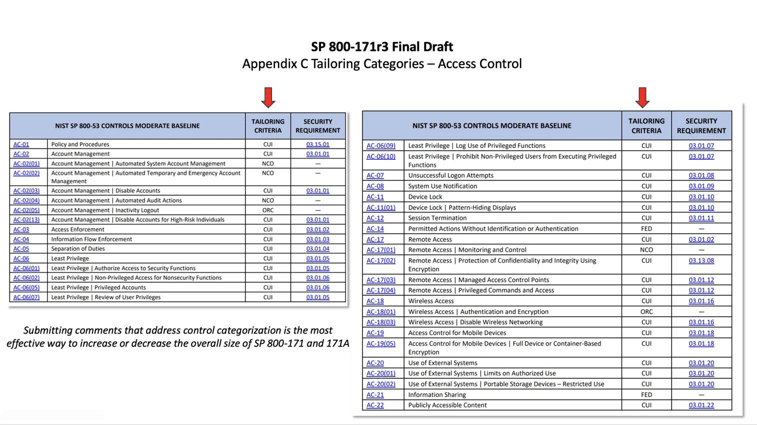
Check out the extended clip from Sum IT Up: Live at CS2 Denver for more details and an explanation on how to use the comment creation flowchart.
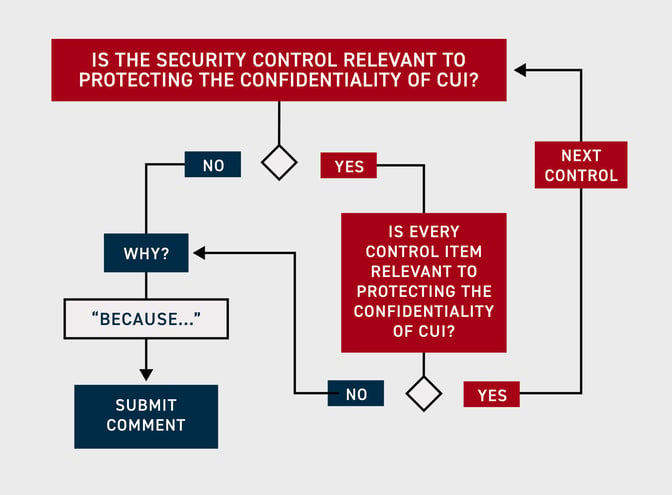
Comments are due by January 12th, 2024. Be sure to use the comment template provided by NIST.
7) Even though revision 3 will bring many changes, the steps to achieving CMMC are still the same.

Steps to CMMC Compliance
The urgent need for companies to become CMMC compliant is clear, but what are the steps businesses should take? Here are seven steps for companies to follow in order to become CMMC compliant.
- Identify the appropriate CMMC level
- Identify assets for CMMC
- Choose a technical design for your CMMC compliance: All-In vs Enclave
- Consider Microsoft Government for your CMMC compliance
- Find a Managed Service Provider (MSP) / Managed Security Service Provider (MSSP)
- Prepare for a third party CMMC assessment
- Complete a CMMC assessment



.jpg)
