U.S. Sues Georgia Tech: A CMMC Wake-Up Call for Higher Ed [+ Expert Advice from University IT Leaders]
Learn about the recent suit filed against Georgia Tech by the U.S. under the False Claims Act and the impending regulations coming to universities with DoD contracts. Get expert advice to prepare your school for a successful CMMC assessment.
The United States Files a False Claims Act (FCA) Suit Against Georgia Tech Due To Cybersecurity Violations
The recent lawsuit filed by the United States against Georgia Tech serves as a startling reminder to higher education institutions doing regulated research for the DoD of the severe consequences if they don't comply with cybersecurity regulations.
Universities are facing increasing scrutiny from the federal government, and that scrutiny will only increase as the Cybersecurity Maturity Model Certification (CMMC) ruling is finalized and rolls into contracts. The CMMC rule will requires a 3rd party (C3PAO) to assess whether universities have implemented the security measures of NIST SP 800-171, which is already required in their contract's DFARS clause.

“Government contractors that fail to fully implement required cybersecurity controls jeopardize the confidentiality of sensitive government information,” said Principal Deputy Assistant Attorney General Brian M. Boynton, head of the Justice Department’s Civil Division. “The department’s Civil Cyber-Fraud Initiative was designed to identify such contractors and to hold them accountable.”
The case against Georgia Tech isn't isolated. It's a manifestation of the broader regulatory push seen in cases like the recent False Claims Act (FCA) suit against Penn State University, where non-compliance with cybersecurity standards related to Covered Defense Information (CDI) under the DFARS 7012 clause resulted in federal action. As more institutions enter the realm of Department of Defense (DoD) contract work, higher education is becoming a significant focus for federal regulators. Schools must recognize that the stakes are rising, and failure to take compliance seriously could result in lawsuits that tarnish their reputation and drain resources.
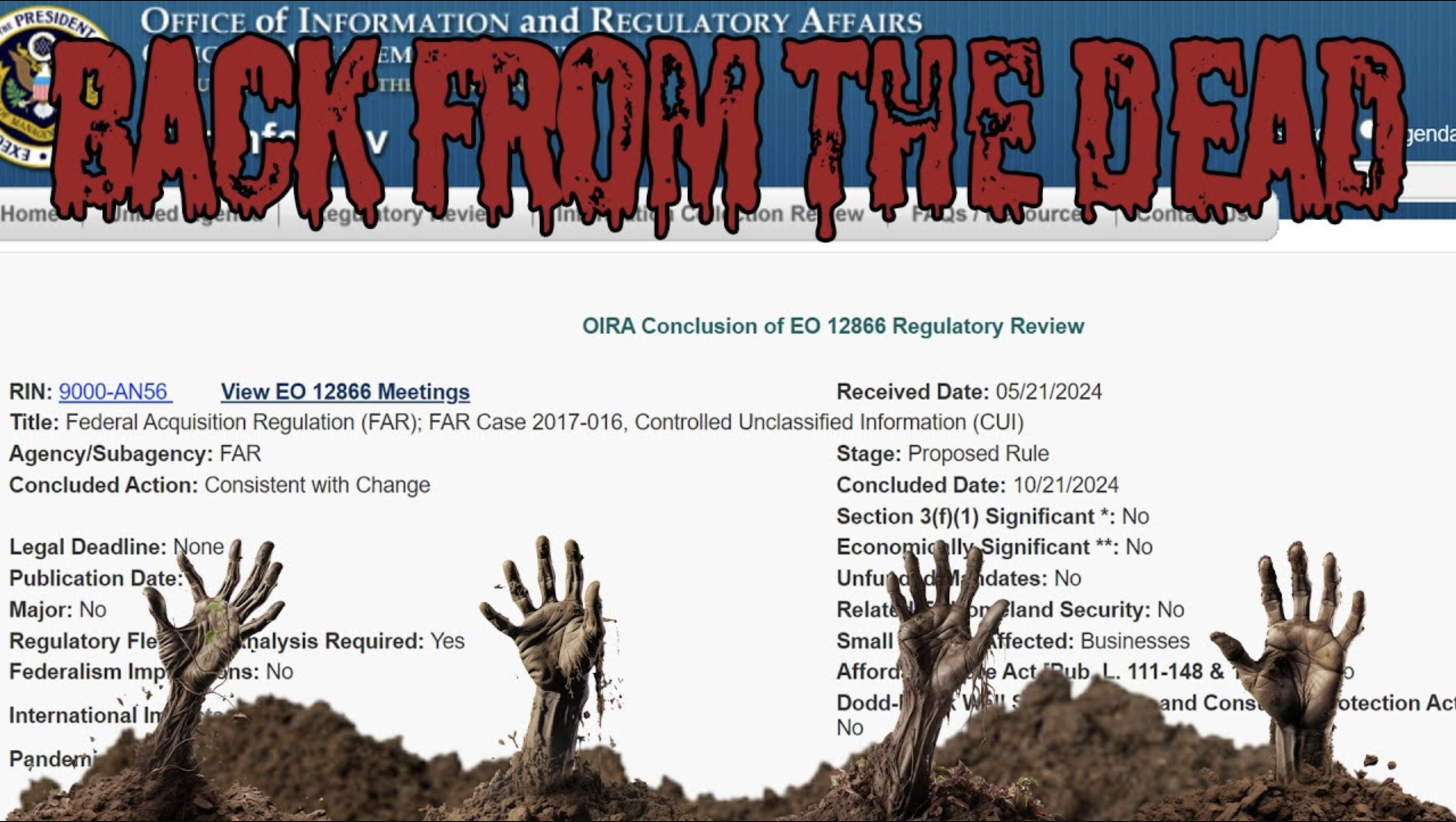
Mounting Pressure: The New Department of Education CUI Rule
If all that wasn't enough to get universities moving toward compliance, the Department of Education recently announced plans to issue a new proposed rule this Fall: 𝗖𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗦𝘁𝗮𝗻𝗱𝗮𝗿𝗱𝘀 𝗳𝗼𝗿 𝗜𝗻𝘀𝘁𝗶𝘁𝘂𝘁𝗶𝗼𝗻𝘀 𝗼𝗳 𝗛𝗶𝗴𝗵𝗲𝗿 𝗘𝗱𝘂𝗰𝗮𝘁𝗶𝗼𝗻 𝘁𝗼 𝗖𝗼𝗺𝗽𝗹𝘆 𝗪𝗶𝘁𝗵 𝗘𝗢 𝟭𝟯𝟱𝟱𝟲 𝗮𝗻𝗱 𝗡𝗜𝗦𝗧 𝟴𝟬𝟬-𝟭𝟳𝟭.
From the abstract of the rule:
"𝘛𝘩𝘦 𝘋𝘦𝘱𝘢𝘳𝘵𝘮𝘦𝘯𝘵 𝘳𝘦𝘭𝘪𝘦𝘴 𝘰𝘯 𝘴𝘤𝘩𝘰𝘰𝘭𝘴 𝘱𝘢𝘳𝘵𝘪𝘤𝘪𝘱𝘢𝘵𝘪𝘯𝘨 𝘪𝘯 𝘵𝘩𝘦 𝘧𝘦𝘥𝘦𝘳𝘢𝘭 𝘴𝘵𝘶𝘥𝘦𝘯𝘵 𝘧𝘪𝘯𝘢𝘯𝘤𝘪𝘢𝘭 𝘢𝘴𝘴𝘪𝘴𝘵𝘢𝘯𝘤𝘦 𝘱𝘳𝘰𝘨𝘳𝘢𝘮𝘴 𝘢𝘯𝘥 𝘰𝘵𝘩𝘦𝘳 𝘨𝘳𝘢𝘯𝘵 𝘱𝘳𝘰𝘨𝘳𝘢𝘮𝘴 𝘶𝘯𝘥𝘦𝘳 𝘵𝘩𝘦 𝘏𝘪𝘨𝘩𝘦𝘳 𝘌𝘥𝘶𝘤𝘢𝘵𝘪𝘰𝘯 𝘈𝘤𝘵 𝘰𝘧 1965, 𝘢𝘴 𝘢𝘮𝘦𝘯𝘥𝘦𝘥 (𝘏𝘌𝘈), 𝘵𝘰 𝘩𝘦𝘭𝘱 𝘤𝘢𝘳𝘳𝘺 𝘰𝘶𝘵 𝘢 𝘸𝘪𝘥𝘦 𝘳𝘢𝘯𝘨𝘦 𝘰𝘧 𝘣𝘶𝘴𝘪𝘯𝘦𝘴𝘴 𝘧𝘶𝘯𝘤𝘵𝘪𝘰𝘯𝘴. 𝘚𝘤𝘩𝘰𝘰𝘭𝘴 𝘳𝘰𝘶𝘵𝘪𝘯𝘦𝘭𝘺 𝘱𝘳𝘰𝘤𝘦𝘴𝘴, 𝘴𝘵𝘰𝘳𝘦, 𝘢𝘯𝘥 𝘵𝘳𝘢𝘯𝘴𝘮𝘪𝘵 𝘊𝘰𝘯𝘵𝘳𝘰𝘭𝘭𝘦𝘥 𝘜𝘯𝘤𝘭𝘢𝘴𝘴𝘪𝘧𝘪𝘦𝘥 𝘐𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 (𝘊𝘜𝘐), 𝘸𝘩𝘪𝘤𝘩 𝘪𝘯𝘤𝘭𝘶𝘥𝘦𝘴 𝘱𝘦𝘳𝘴𝘰𝘯𝘢𝘭𝘭𝘺 𝘪𝘥𝘦𝘯𝘵𝘪𝘧𝘪𝘢𝘣𝘭𝘦 𝘪𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 (𝘗𝘐𝘐), 𝘴𝘦𝘯𝘴𝘪𝘵𝘪𝘷𝘦 𝘱𝘦𝘳𝘴𝘰𝘯𝘢𝘭𝘭𝘺 𝘪𝘥𝘦𝘯𝘵𝘪𝘧𝘪𝘢𝘣𝘭𝘦 𝘪𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 (𝘚𝘗𝘐𝘐), 𝘢𝘯𝘥 𝘪𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯. 𝘛𝘩𝘦 𝘱𝘳𝘰𝘵𝘦𝘤𝘵𝘪𝘰𝘯 𝘰𝘧 𝘴𝘦𝘯𝘴𝘪𝘵𝘪𝘷𝘦 𝘥𝘢𝘵𝘢 𝘸𝘩𝘪𝘭𝘦 𝘳𝘦𝘴𝘪𝘥𝘪𝘯𝘨 𝘪𝘯 𝘴𝘤𝘩𝘰𝘰𝘭 𝘪𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 𝘴𝘺𝘴𝘵𝘦𝘮𝘴 𝘪𝘴 𝘰𝘧 𝘱𝘢𝘳𝘢𝘮𝘰𝘶𝘯𝘵 𝘪𝘮𝘱𝘰𝘳𝘵𝘢𝘯𝘤𝘦 𝘵𝘰 𝘵𝘩𝘦 𝘋𝘦𝘱𝘢𝘳𝘵𝘮𝘦𝘯𝘵.
𝘛𝘰 𝘢𝘴𝘴𝘶𝘳𝘦 𝘴𝘤𝘩𝘰𝘰𝘭𝘴 𝘱𝘳𝘰𝘱𝘦𝘳𝘭𝘺 𝘱𝘳𝘰𝘵𝘦𝘤𝘵 𝘊𝘜𝘐, 𝘢𝘴 𝘳𝘦𝘲𝘶𝘪𝘳𝘦𝘥 𝘣𝘺 𝘌𝘹𝘦𝘤𝘶𝘵𝘪𝘷𝘦 𝘖𝘳𝘥𝘦𝘳 13556, 𝘢𝘯𝘥 𝘵𝘩𝘦 𝘳𝘦𝘨𝘶𝘭𝘢𝘵𝘪𝘰𝘯𝘴 𝘢𝘵 32 𝘊𝘍𝘙 𝘱𝘢𝘳𝘵 2002 𝘸𝘩𝘪𝘤𝘩 𝘳𝘦𝘲𝘶𝘪𝘳𝘦 𝘯𝘰𝘯-𝘍𝘦𝘥𝘦𝘳𝘢𝘭 𝘦𝘯𝘵𝘪𝘵𝘪𝘦𝘴 𝘩𝘢𝘯𝘥𝘭𝘪𝘯𝘨 𝘊𝘜𝘐 𝘵𝘰 𝘪𝘮𝘱𝘭𝘦𝘮𝘦𝘯𝘵 𝘕𝘐𝘚𝘛 800-171 𝘗𝘳𝘰𝘵𝘦𝘤𝘵𝘪𝘯𝘨 𝘊𝘰𝘯𝘵𝘳𝘰𝘭𝘭𝘦𝘥 𝘜𝘯𝘤𝘭𝘢𝘴𝘴𝘪𝘧𝘪𝘦𝘥 𝘐𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 𝘪𝘯 𝘕𝘰𝘯𝘧𝘦𝘥𝘦𝘳𝘢𝘭 𝘚𝘺𝘴𝘵𝘦𝘮𝘴 𝘢𝘯𝘥 𝘖𝘳𝘨𝘢𝘯𝘪𝘻𝘢𝘵𝘪𝘰𝘯𝘴 (𝘕𝘐𝘚𝘛 800-171), 𝘵𝘩𝘦 𝘋𝘦𝘱𝘢𝘳𝘵𝘮𝘦𝘯𝘵 𝘱𝘭𝘢𝘯𝘴 𝘵𝘰 𝘱𝘳𝘰𝘱𝘰𝘴𝘦 𝘵𝘰 𝘳𝘦𝘨𝘶𝘭𝘢𝘵𝘦 𝘰𝘯 𝘪𝘯𝘧𝘰𝘳𝘮𝘢𝘵𝘪𝘰𝘯 𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘳𝘦𝘲𝘶𝘪𝘳𝘦𝘮𝘦𝘯𝘵𝘴."
Feeling overwhelmed yet? Don't worry, we brought help.
Learn From University IT Leaders Taking on CMMC Successfully
At CS2 Denver, Daniel Akridge, Director of Client Engagement at Summit 7, moderated a panel featuring university IT leaders who discussed their experiences with NIST 800-171 compliance under DFARS 7012. The conversation made it clear that the compliance journey for universities is unique, given their decentralized nature.
In the remainder of this blog, you will find key takeaways from their discussion and solutions to common compliance challenges faced by universities, like:
- Who is actually responsible for compliance at a university?
- How do you communicate the importance of compliance investment with leaders?
- What are strategies that universities can use to strike the balance between compliance cost and risk?
By understanding who is responsible for compliance, how to communicate the importance of investing in it, and adopting key strategies to balance cost and risk, universities can protect themselves from the kind of regulatory scrutiny currently enveloping Georgia Tech and Penn State.
Watch the full CS2 panel discussion here:
Who is Responsible for University Compliance?
The panelists shared that their IT departments do not own the responsibility of compliance. IT can serve as the translator of compliance requirements for higher ups, communicating the cost and risk clearly, but decision-making around priorities and investment is not their job. Their advice? Don’t be afraid to push back. Just because you are the one that understands it doesn’t mean that all the decisions should be pushed down to you.
And yet, even when their proper level of responsibility is clarified, the weight of keeping up with all the compliance requirements is immense: “It’s kind of like collecting cards, and every single day you get a new card,” said Melissa Kimble of the University of Maine, “you have to go look at your card and see what regulation you need to read for this particular card, [then] what’s required for this particular card to use it.”
The need to stay up to date and find supportive camaraderie for the unique trials of higher education DoD contracts has brought about a high level of collaboration among the panelists and their peers. They have a busy Slack channel dedicated to the task, and a group for NIST 800-171 on Educause.edu.
If you are in the higher ed compliance world: don’t go it alone.
How do I Communicate the Importance of Compliance Investment to My Leadership?
One of the more frustrating parts of your job is likely sharing the priority of compliance with others in the university ecosystem. Playing the devil’s advocate, the host, Daniel, posed the question that the panelists receive frequently:
“But doesn’t compliance slow down research?”
“If you pose that question to faculty the answer will always be "absolutely" - and that is unacceptable,” responded Jay Gallman, from Duke University. Holding ground with the importance of risk-mitigation is crucial, but it creates a tension with higher up budget-watchers and researchers who resist added restrictions. “We can bring them to the truth but we can’t make them accept the truth,” said Kolin Hodgson from the University of Notre Dame.
So, what is that truth they bring to their leadership? Penn State. On September 1, 2023, a False Claims Act (FCA) lawsuit against Penn State University was unveiled by the U.S. District Court for the Eastern District of Pennsylvania. The core accusations in this legal action center on claims that Penn State did not adhere to the mandated cybersecurity standards for Covered Defense Information (CDI) outlined in the DFARS 252.204-7012 clause.
“Never let a good crisis go to waste,” Hodgson told Daniel. “When the Penn St. story broke we immediately elevated the information to the highest levels of our university to make sure that everyone was aware that it was going on.” For the panelists, Penn St. is a helpful portent to send up the chain to signal the risk. “If somebody wasn’t thinking about risk as they make decisions about what money they will spend to become [compliant and secure], this is one more piece of evidence on that risk side,” said Hodgson.
The suits against Penn State and Georgia Tech are powerful tools in your hands to convince leadership that the investment is worth it, and the time is now.
Two Strategies for Striking the Balance Between Compliance Cost and Risk
Strategy #1: Build an Enclave
The biggest hurdle of implementing the extensive NIST 800-171 protocols for universities is the unique nature of the organization. “The university is not a business…it’s 300 businesses under one roof,” Hodgson shared. “So, an enclave is really a good choice. Universities really tend to gravitate there because the choice to make the entire university CMMC compliant is probably not a good choice.”
A CUI Enclave is a secure area or system where measures are implemented to control access, monitor activities, and ensure compliance with NIST 800-171 regulations governing the handling of CUI.

Another issue unique to the university setting is the tension between compliance and collaboration. How do you mitigate risk in an environment where sensitive US export control data is being handled and foreign nationals are studying?
“You have to have an enclave,” Kimble shared. An enclave will have another set of devices, just like your normal workstations – but that are compliant - making the cost of implementation manageable, especially when compared to scoping the whole university.
Strategy #2: Hire an MSP to Manage the Enclave
The managed enclave is a perfect solution for higher education compliance, but it also adds a problem: the number of devices to be managed doubles. “We here at higher ed are becoming Noah’s Ark: we have to have two of everything,” Gallman joked. Double the devices means double the managing workload, which again exacerbates the cost/risk tension.
The panelists shared that the solution most universities are turning to is a Managed Service Provider (MSP), a third-party organization that is brought in to build out and manage this secure enclave for the university. “We’ve had to because we couldn’t afford to pay salaries for additional folks to come in,” Kimble shared.
The other option would be to not just double the amount of technology needed, but also double the number of IT personnel. “[It is difficult] to find people with the right skills,” said Wendy Epley of the University of Arizona. “How do we find someone that understands not just FIPS, but also NIST 800-171?”
According to the panelists, the combination of building out an enclave and having it managed by an MSP is the perfect, balanced solution to the unique problems of the university setting of DoD contract work.
What if We're a University Just Starting Our Compliance Journey?
The panelists offered two pieces of advice for those just getting started, offering the wisdom they wish they had known at the beginning:
Communicate Expectations
Communicating expectations is paramount for success. The first, from Melissa Kimble, was to “push everything up the chain so you can educate your researchers, [and] have it in your contracts so you can negotiate early on.” Melissa encouraged anyone who is just getting started to inform higher up leaders of their responsibility before signing regulated research contracts; to do your due diligence to ensure that everything required to execute the contract within compliance has been planned for and baked into communication to all involved parties.
Find your CUI
The second piece of advice was to make sure you understand where everything is. Before the contracts, be rigorously detailed in creating a data flow diagram. If it’s not clear what is CUI and what isn’t, ask questions and keep asking until it’s clear. CMMC is all about protecting CUI, but you can't protect something until you know where it is. If you don't have a good way of finding and handling CUI, check out the video below to see how Microsoft Purview can help.
If you represent a university just beginning your compliance journey, or if you are down the road a bit and need help getting to the finish line, we're here to help.
With over 1,000 clients, Summit 7 is the #1 MSP/MSSP for the Defense Industrial Base.
We provide tailored Microsoft solutions for universities doing DoD regulated research so schools can tackle compliance with confidence.
Enter your information below to speak with one of our CMMC experts today: